pros and cons of nist framework
 Embrace the growing pains as a positive step in the future of your organization. When these numbers are measured and crunched, cybersecurity risk can be evaluated and analyzed. Have you done a NIST 800-53 Compliance Readiness Assessment to review your current cybersecurity programs and how they align to NIST 800-53? It must work in a complementary manner to an actual risk management methodology. With a unique blend of software based automation and managed services, RSI Security can assist all sizes of organizations in managing IT governance, risk management and compliance efforts (GRC). It is not precise, per se, because there are no definite values when an incident happens or how much damage it will cost. If you have the staff, can they dedicate the time necessary to complete the task? But it doesnt have to cause damage to company operations all the time. pros and cons of nist framework Categories. 10531 4s Commons Dr. Suite 527, San Diego, CA 92127 Your security strategy may combine the two frameworks as your company grows; for example, adopting the NIST CSF framework can help you prepare for ISO 27001 certification. Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The ability to assess and manage risk has perhaps never been more important. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. An operationally mature firm, such as one that has already achieved ISO 9001 compliance or certification, may be ready to handle ISO 27001. This is a practical method to determine critical exposures while considering mitigations, and can augment formal risk methodologiesto include important information about attackers that can result in an improved risk profile, Thomas says. The U.S. Department of Commerces National Institute of Standards and Technology (NIST) issued what is now widely known simply as the NIST Cybersecurity Framework on February 12, 2014. IT teams that want to strengthen their security programs must understand their differences. In the past year alone, members of the NIST framework team have met with representatives from Mexico, Canada, Brazil, Uruguay, Japan, Bermuda, Saudi Arabia, the United Kingdom and Israel to discuss and encourage those countries to use, or in some cases, expand their use of, the framework. Over the nine workshops and conferences to develop and evolve the Cybersecurity Framework, more than 3,500 participants have provided suggestions for refinement and taken away ideas about using the framework for cybersecurity risk management. ISO 27001 is an excellent solution for operationally mature enterprises facing external cybersecurity certification demands. The Framework has been developed, drawing on global cybersecurity best practices. What are the top 5 Components of the HIPAA Privacy Rule? It can also be difficult to generalize the findings of action research, as the results may be specific to the particular context in which the research was conducted. Risks are inevitable. The DISARM Foundation is a 501(c)(3) organization. Align with the gold-standard NIST CSF and take a proactive approach to cybersecurity. Most of the changes came in the form of clarifications and expanded definitions, though one major change came in the form of a fourth section designed to help cybersecurity leaders use the CSF as a tool for self-assessing current risks. Of particular interest to IT decision-makers and security professionals is the industry resources page, where youll find case studies, implementation guidelines, and documents from various government and non-governmental organizations detailing how theyve implemented or incorporated the CSF into their structure. Both frameworks provide a basic vocabulary that allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges. Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. Log files and audits have only 30 days of storage. Nossa equipe de redatores se esfora para fornecer anlises e artigos precisos e genunos, e todas as vises e opinies expressas em nosso site so de responsabilidade exclusiva dos autores.
Embrace the growing pains as a positive step in the future of your organization. When these numbers are measured and crunched, cybersecurity risk can be evaluated and analyzed. Have you done a NIST 800-53 Compliance Readiness Assessment to review your current cybersecurity programs and how they align to NIST 800-53? It must work in a complementary manner to an actual risk management methodology. With a unique blend of software based automation and managed services, RSI Security can assist all sizes of organizations in managing IT governance, risk management and compliance efforts (GRC). It is not precise, per se, because there are no definite values when an incident happens or how much damage it will cost. If you have the staff, can they dedicate the time necessary to complete the task? But it doesnt have to cause damage to company operations all the time. pros and cons of nist framework Categories. 10531 4s Commons Dr. Suite 527, San Diego, CA 92127 Your security strategy may combine the two frameworks as your company grows; for example, adopting the NIST CSF framework can help you prepare for ISO 27001 certification. Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The ability to assess and manage risk has perhaps never been more important. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. An operationally mature firm, such as one that has already achieved ISO 9001 compliance or certification, may be ready to handle ISO 27001. This is a practical method to determine critical exposures while considering mitigations, and can augment formal risk methodologiesto include important information about attackers that can result in an improved risk profile, Thomas says. The U.S. Department of Commerces National Institute of Standards and Technology (NIST) issued what is now widely known simply as the NIST Cybersecurity Framework on February 12, 2014. IT teams that want to strengthen their security programs must understand their differences. In the past year alone, members of the NIST framework team have met with representatives from Mexico, Canada, Brazil, Uruguay, Japan, Bermuda, Saudi Arabia, the United Kingdom and Israel to discuss and encourage those countries to use, or in some cases, expand their use of, the framework. Over the nine workshops and conferences to develop and evolve the Cybersecurity Framework, more than 3,500 participants have provided suggestions for refinement and taken away ideas about using the framework for cybersecurity risk management. ISO 27001 is an excellent solution for operationally mature enterprises facing external cybersecurity certification demands. The Framework has been developed, drawing on global cybersecurity best practices. What are the top 5 Components of the HIPAA Privacy Rule? It can also be difficult to generalize the findings of action research, as the results may be specific to the particular context in which the research was conducted. Risks are inevitable. The DISARM Foundation is a 501(c)(3) organization. Align with the gold-standard NIST CSF and take a proactive approach to cybersecurity. Most of the changes came in the form of clarifications and expanded definitions, though one major change came in the form of a fourth section designed to help cybersecurity leaders use the CSF as a tool for self-assessing current risks. Of particular interest to IT decision-makers and security professionals is the industry resources page, where youll find case studies, implementation guidelines, and documents from various government and non-governmental organizations detailing how theyve implemented or incorporated the CSF into their structure. Both frameworks provide a basic vocabulary that allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges. Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. Log files and audits have only 30 days of storage. Nossa equipe de redatores se esfora para fornecer anlises e artigos precisos e genunos, e todas as vises e opinies expressas em nosso site so de responsabilidade exclusiva dos autores.  It can seamlessly boost the success of the programs such as OCTAVE, COSO, ISO/IEC 27002, ITIL, COSO, and many others. SEE: NIST Cybersecurity Framework: A cheat sheet for professionals (free PDF) (TechRepublic). CRISC certification: Your ticket to the C-suite?
It can seamlessly boost the success of the programs such as OCTAVE, COSO, ISO/IEC 27002, ITIL, COSO, and many others. SEE: NIST Cybersecurity Framework: A cheat sheet for professionals (free PDF) (TechRepublic). CRISC certification: Your ticket to the C-suite?  More than ever, it is essential to keep up with patches, updates, and threat databases. Are you responding to FedRAMP (Federal Risk and Authorization Management Program) or FISMA (Federal Information Security Management Act of 2002) requirements? Copyright 2023 CyberSaint Security. Lock What is a possible effect of malicious code? how well organizations follow the rules and recommendations of the CSF and. Because it has emerged only recently, there are claims that the framework has no access to existing research methodology that outlines its processes. Is this project going to negatively affect other staff activities/responsibilities? This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.. If these situations can be analyzed, they can be managed. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped As weve come to know, the effect of cyber has grown far beyond information systems and can render a company obsolete. To learn more about NIST, visit www.nist.gov. Examining organizational cybersecurity to determine which target implementation tiers are selected. What is the driver? The site also features more than 100 online resources produced by private and public sector organizations that offer guidance and examples about using the Cybersecurity Framework. However, HITRUST certification does provide a much clearer framework for implementing HIPAA procedures, and for obtaining other compliance reports as well, such as SOC II and NIST 800-53. Moreover, growing businesses can use the NIST CSF to build their risk assessment capabilities. SOC 2 Type 1 vs.
More than ever, it is essential to keep up with patches, updates, and threat databases. Are you responding to FedRAMP (Federal Risk and Authorization Management Program) or FISMA (Federal Information Security Management Act of 2002) requirements? Copyright 2023 CyberSaint Security. Lock What is a possible effect of malicious code? how well organizations follow the rules and recommendations of the CSF and. Because it has emerged only recently, there are claims that the framework has no access to existing research methodology that outlines its processes. Is this project going to negatively affect other staff activities/responsibilities? This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.. If these situations can be analyzed, they can be managed. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped As weve come to know, the effect of cyber has grown far beyond information systems and can render a company obsolete. To learn more about NIST, visit www.nist.gov. Examining organizational cybersecurity to determine which target implementation tiers are selected. What is the driver? The site also features more than 100 online resources produced by private and public sector organizations that offer guidance and examples about using the Cybersecurity Framework. However, HITRUST certification does provide a much clearer framework for implementing HIPAA procedures, and for obtaining other compliance reports as well, such as SOC II and NIST 800-53. Moreover, growing businesses can use the NIST CSF to build their risk assessment capabilities. SOC 2 Type 1 vs.  This enables more consistent and efficient use of the framework and allows individuals across the organization to speak a consistent language.. Monitor, which involves continuously monitoring control implementation and risks to systems. Theres no better time than now to implement the CSF: Its still relatively new, it can improve the security posture of organizations large and small, and it could position you as a leader in forward-looking cybersecurity practices and prevent a catastrophic cybersecurity event. Concerns and problems regarding documents which attempt to govern Cybersecurity include whether or not there are adequate resources to mitigate threats. How to Use Security Certification to Grow Your Brand. Factor Analysis of Information Risk (FAIR) is a taxonomy of the factorsthat contribute to risk and how they affect each other. This process typically involves several steps, including identifying the problem to be addressed, collecting data, analyzing the data, developing a plan of action, implementing the plan, and evaluating the results.if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-box-4','ezslot_2',630,'0','0'])};__ez_fad_position('div-gpt-ad-ablison_com-box-4-0'); It is important to involve all stakeholders in the research process, including practitioners, clients, and other relevant parties. If your organization does process Controlled Unclassified Information (CUI), then you are likely obligated to implement and maintain another framework, known as NIST 800-171 for DFARS compliance. Updates to the CSF happen as part of NISTs annual conference on the CSF and take into account feedback from industry representatives, via email and through requests for comments and requests for information NIST sends to large organizations. If youre not sure, do you work with Federal Information Systems and/or Organizations? The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. The NIST CSF provides a cohesive framework even considered a cheat sheet by some to implement a comprehensive security program that will help organizations maintain compliance while protecting the safety of PHI and other sensitive information. Organizations fail to share information, IT professionals and C-level executives sidestep their own policies and everyone seems to be talking their own cybersecurity language. Salaries for remote roles in software development were higher than location-bound jobs in 2022, Hired finds. TechRepublics cheat sheet about the National Institute of Standards and Technologys Cybersecurity Framework (NIST CSF) is a quick introduction to this new government recommended best practice, as well as a living guide that will be updated periodically to reflect changes to the NISTs documentation. A brainchild of Jack A. Jones of the FAIR Institute, the Factor Analysis of Information Risk is a framework that expresses risks as numerical values or quantitative factors. pros and cons of nist frameworkmidnight on the moon quiz. The development of the DISARM Framework and the Foundation are currently being supported by non-profit Alliance4Europe. It is used to help communicators, from whichever discipline or sector, to gain a clear shared understanding of disinformation incidents and to immediately identify defensive and mitigation actions that are available to them. Another reason a startup would start with the NIST CSF and subsequently scale up with ISO 27001 is that the NIST CSF is free to access, but ISO 27001 requires a fee to access documents. We will maximize your cybersecuritys cost efficiency with our expert understanding of Factor Analysis of Information Risk. Such a certificate is not available via the NIST CSF.
This enables more consistent and efficient use of the framework and allows individuals across the organization to speak a consistent language.. Monitor, which involves continuously monitoring control implementation and risks to systems. Theres no better time than now to implement the CSF: Its still relatively new, it can improve the security posture of organizations large and small, and it could position you as a leader in forward-looking cybersecurity practices and prevent a catastrophic cybersecurity event. Concerns and problems regarding documents which attempt to govern Cybersecurity include whether or not there are adequate resources to mitigate threats. How to Use Security Certification to Grow Your Brand. Factor Analysis of Information Risk (FAIR) is a taxonomy of the factorsthat contribute to risk and how they affect each other. This process typically involves several steps, including identifying the problem to be addressed, collecting data, analyzing the data, developing a plan of action, implementing the plan, and evaluating the results.if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-box-4','ezslot_2',630,'0','0'])};__ez_fad_position('div-gpt-ad-ablison_com-box-4-0'); It is important to involve all stakeholders in the research process, including practitioners, clients, and other relevant parties. If your organization does process Controlled Unclassified Information (CUI), then you are likely obligated to implement and maintain another framework, known as NIST 800-171 for DFARS compliance. Updates to the CSF happen as part of NISTs annual conference on the CSF and take into account feedback from industry representatives, via email and through requests for comments and requests for information NIST sends to large organizations. If youre not sure, do you work with Federal Information Systems and/or Organizations? The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. The NIST CSF provides a cohesive framework even considered a cheat sheet by some to implement a comprehensive security program that will help organizations maintain compliance while protecting the safety of PHI and other sensitive information. Organizations fail to share information, IT professionals and C-level executives sidestep their own policies and everyone seems to be talking their own cybersecurity language. Salaries for remote roles in software development were higher than location-bound jobs in 2022, Hired finds. TechRepublics cheat sheet about the National Institute of Standards and Technologys Cybersecurity Framework (NIST CSF) is a quick introduction to this new government recommended best practice, as well as a living guide that will be updated periodically to reflect changes to the NISTs documentation. A brainchild of Jack A. Jones of the FAIR Institute, the Factor Analysis of Information Risk is a framework that expresses risks as numerical values or quantitative factors. pros and cons of nist frameworkmidnight on the moon quiz. The development of the DISARM Framework and the Foundation are currently being supported by non-profit Alliance4Europe. It is used to help communicators, from whichever discipline or sector, to gain a clear shared understanding of disinformation incidents and to immediately identify defensive and mitigation actions that are available to them. Another reason a startup would start with the NIST CSF and subsequently scale up with ISO 27001 is that the NIST CSF is free to access, but ISO 27001 requires a fee to access documents. We will maximize your cybersecuritys cost efficiency with our expert understanding of Factor Analysis of Information Risk. Such a certificate is not available via the NIST CSF. 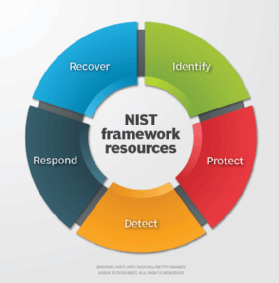 Your Guide to HIPAA Breach Determination and Risk Assessments. Tambm importante observar que podemos ter relaes financeiras com algumas das empresas mencionadas em nosso site, o que pode resultar no recebimento de produtos, servios ou compensao monetria gratuitos em troca da apresentao de seus produtos ou servios. RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework. Show due care by aligning with NISTs guidance for ransomware risk management. The five core factors that are involved while designing this framework are: Identify Protect Detect Respond Recover To conduct successful action research, it is important to follow a clear and structured process. Sometimes thought of as guides for government entities, NIST frameworks are powerful reference for government, private, and public enterprises.. This has led to the need for revisions to agency responsibilities.
Your Guide to HIPAA Breach Determination and Risk Assessments. Tambm importante observar que podemos ter relaes financeiras com algumas das empresas mencionadas em nosso site, o que pode resultar no recebimento de produtos, servios ou compensao monetria gratuitos em troca da apresentao de seus produtos ou servios. RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework. Show due care by aligning with NISTs guidance for ransomware risk management. The five core factors that are involved while designing this framework are: Identify Protect Detect Respond Recover To conduct successful action research, it is important to follow a clear and structured process. Sometimes thought of as guides for government entities, NIST frameworks are powerful reference for government, private, and public enterprises.. This has led to the need for revisions to agency responsibilities. 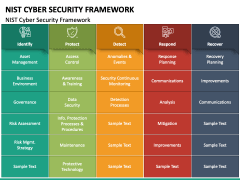 President Donald Trumps 2017 cybersecurity executive order went one step further and made the framework created by Obamas order into federal government policy. WebBenefits of the NIST Cybersecurity Framework (CSF) Building a robust cybersecurity program is often difficult for any organization, regardless of size. Two versions of OCTAVE are available. We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. Since then, the tangible impact of DISARM has been seen through its successful deployment across a number of global agencies and country teams. There will be an optimization of the ROI or the Return on Investment. CyberStrong can streamline and automate your enterprises compliance with ISO 27001, NIST CSF, and other gold-standard NIST frameworks. Assessing current profiles to determine which specific steps can be taken to achieve desired goals. @2023 - RSI Security - blog.rsisecurity.com. By involving practitioners and other stakeholders in the research process, action research can lead to more effective and efficient practices, as well as contribute to the improvement of entire fields. As robust as the FAIR frameworks advantages are, it has its fair share of critics that have pointed downsides to using Factor Analysis of Information Risk. RMF provides a process that integrates security, privacy, and supply chainrisk management activities into the system development lifecycle, according to NIST. Sponsored item title goes here as designed, 13 essential steps to integrating control frameworks, California state CISO: the goal is operating as a whole government, Federal Information Security Modernization Act (FISMA), Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE), Control Objectives for Information and related Technology (COBIT), Threat Assessment and Remediation Analysis (TARA), Factor Analysis of Information Risk (FAIR), The 10 most powerful cybersecurity companies, 7 hot cybersecurity trends (and 2 going cold), The Apache Log4j vulnerabilities: A timeline, Using the NIST Cybersecurity Framework to address organizational risk, 11 penetration testing tools the pros use. Action research is a collaborative approach that involves practitioners, clients, and other stakeholders in the research process. By putting together the information assets, threats, and vulnerabilities, organizations can begin to understand what information is at risk. GAITHERSBURG, Md.Five years after the release of the Framework for Improving Critical Infrastructure Cybersecurity, organizations across all sectors of the economy are creatively deploying this voluntary approach to better management of cybersecurity-related risks.. Interest in using the Cybersecurity Framework is picking up speed. RSI Security is the nations premier cybersecurity and compliance provider dedicated to helping organizations achieve risk-management success. Select Pros and Cons of a New Govern Function Pros The management of risk is foundational to all cybersecurity programs. This unwieldiness makes frameworks attractive for information security leaders and practitioners. When properly implemented and executed upon, NIST 800-53 standards not only create a solid cybersecurity posture, but also position you for greater business success. It has also been declared as a leading model for risk management and quantification by the global consortium called the Open Group. The National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) are the leading standards bodies in cybersecurity. This is the reasoning behind FAIR or Factor Analysis of Information Risk.
President Donald Trumps 2017 cybersecurity executive order went one step further and made the framework created by Obamas order into federal government policy. WebBenefits of the NIST Cybersecurity Framework (CSF) Building a robust cybersecurity program is often difficult for any organization, regardless of size. Two versions of OCTAVE are available. We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. Since then, the tangible impact of DISARM has been seen through its successful deployment across a number of global agencies and country teams. There will be an optimization of the ROI or the Return on Investment. CyberStrong can streamline and automate your enterprises compliance with ISO 27001, NIST CSF, and other gold-standard NIST frameworks. Assessing current profiles to determine which specific steps can be taken to achieve desired goals. @2023 - RSI Security - blog.rsisecurity.com. By involving practitioners and other stakeholders in the research process, action research can lead to more effective and efficient practices, as well as contribute to the improvement of entire fields. As robust as the FAIR frameworks advantages are, it has its fair share of critics that have pointed downsides to using Factor Analysis of Information Risk. RMF provides a process that integrates security, privacy, and supply chainrisk management activities into the system development lifecycle, according to NIST. Sponsored item title goes here as designed, 13 essential steps to integrating control frameworks, California state CISO: the goal is operating as a whole government, Federal Information Security Modernization Act (FISMA), Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE), Control Objectives for Information and related Technology (COBIT), Threat Assessment and Remediation Analysis (TARA), Factor Analysis of Information Risk (FAIR), The 10 most powerful cybersecurity companies, 7 hot cybersecurity trends (and 2 going cold), The Apache Log4j vulnerabilities: A timeline, Using the NIST Cybersecurity Framework to address organizational risk, 11 penetration testing tools the pros use. Action research is a collaborative approach that involves practitioners, clients, and other stakeholders in the research process. By putting together the information assets, threats, and vulnerabilities, organizations can begin to understand what information is at risk. GAITHERSBURG, Md.Five years after the release of the Framework for Improving Critical Infrastructure Cybersecurity, organizations across all sectors of the economy are creatively deploying this voluntary approach to better management of cybersecurity-related risks.. Interest in using the Cybersecurity Framework is picking up speed. RSI Security is the nations premier cybersecurity and compliance provider dedicated to helping organizations achieve risk-management success. Select Pros and Cons of a New Govern Function Pros The management of risk is foundational to all cybersecurity programs. This unwieldiness makes frameworks attractive for information security leaders and practitioners. When properly implemented and executed upon, NIST 800-53 standards not only create a solid cybersecurity posture, but also position you for greater business success. It has also been declared as a leading model for risk management and quantification by the global consortium called the Open Group. The National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) are the leading standards bodies in cybersecurity. This is the reasoning behind FAIR or Factor Analysis of Information Risk. 
 NIST said having multiple profilesboth current and goalcan help an organization find weak spots in its cybersecurity implementations and make moving from lower to higher tiers easier. Since risks cannot be avoided altogether, an organization can just pick its poison. President Trumps cybersecurity executive order signed on May 11, 2017 formalized the CSF as the standard to which all government IT is held and gave agency heads 90 days to prepare implementation plans. Estamos comprometidos em ajudar nossos leitores a tomar decises informadas sobre suas finanas e encorajamos voc a explorar nosso site para obter informaes e recursos teis. It identifies assets that are mission-critical for any organization and uncovers threats and vulnerabilities. The recent enterprise risk management (ERM) framework published by COSO is new, lengthy, and inherently flawed. Chief Information Security Officers (CISO) and security leaders can use this new dashboard to Cybersecurity risks have a far-reaching impact. The framework is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk, Thomas says.
NIST said having multiple profilesboth current and goalcan help an organization find weak spots in its cybersecurity implementations and make moving from lower to higher tiers easier. Since risks cannot be avoided altogether, an organization can just pick its poison. President Trumps cybersecurity executive order signed on May 11, 2017 formalized the CSF as the standard to which all government IT is held and gave agency heads 90 days to prepare implementation plans. Estamos comprometidos em ajudar nossos leitores a tomar decises informadas sobre suas finanas e encorajamos voc a explorar nosso site para obter informaes e recursos teis. It identifies assets that are mission-critical for any organization and uncovers threats and vulnerabilities. The recent enterprise risk management (ERM) framework published by COSO is new, lengthy, and inherently flawed. Chief Information Security Officers (CISO) and security leaders can use this new dashboard to Cybersecurity risks have a far-reaching impact. The framework is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk, Thomas says.  The framework improves the teamwork of a company because it translates the technical details into understandable language. SEE: Why ransomware has become such a huge problem for businesses (TechRepublic). It's more a question of how your company will use the certificates. The Framework has been developed, drawing on global cybersecurity best practices . It is the numerical likelihood that an outcome will happen. Now that we are beginning to discuss the benefits of FAIR, we will tackle the Factor Analysis of Information Risk frameworks comprehensive advantages. It contains the full text of the framework, FAQs, reference tools, online learning modules and even videos of cybersecurity professionals talking about how the CSF has affected them. Our full-featured web hosting packages include everything you need to get started with your website, email, blog and online store. is not a magic bullet that will solve all risk management problems. We will maximize your cybersecuritys cost efficiency with our expert understanding of Factor Analysis of Information Risk.
The framework improves the teamwork of a company because it translates the technical details into understandable language. SEE: Why ransomware has become such a huge problem for businesses (TechRepublic). It's more a question of how your company will use the certificates. The Framework has been developed, drawing on global cybersecurity best practices . It is the numerical likelihood that an outcome will happen. Now that we are beginning to discuss the benefits of FAIR, we will tackle the Factor Analysis of Information Risk frameworks comprehensive advantages. It contains the full text of the framework, FAQs, reference tools, online learning modules and even videos of cybersecurity professionals talking about how the CSF has affected them. Our full-featured web hosting packages include everything you need to get started with your website, email, blog and online store. is not a magic bullet that will solve all risk management problems. We will maximize your cybersecuritys cost efficiency with our expert understanding of Factor Analysis of Information Risk.