WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Additionally, organizations can also help guard against attacks by providing user training on how to better identify phishing emails and malicious websites. These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. DEVELOPER DO NOT SUPPORT ANY OF THE ILLEGAL ACTIVITIES. So it can be used for detection. https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. 4 comments Comments. Here is the work around code to implement this. https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images, Abusing CVE-2022-26923 through SOCKS5 on a Mythic C2 agent, The Auror Project Challenge 1 [Setting the lab up automatically]. Subsequent requests would result in "No embedded JWK in JWS header" error. There are some improvements to Evilginx UI making it a bit more visually appealing. This blog post was written by Varun Gupta. Do Not Sell or Share My Personal Information, StrozFriedbergIncident Response Services, Initial logins from the phishing server will appear as the. Home > Uncategorized > evilginx2 google phishlet. Once the site is up and running, any users who visit the phishing link generated by Evilginx2 will be met with a page that looks identical to a legitimate Microsoft login page. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. I'd like to give out some honorable mentions to people who provided some quality contributions and who made this update happen: Julio @juliocesarfort - For constantly proving to me and himself that the tool works (sometimes even too well)! Similarly Find And Kill Process On other Ports That are in use. 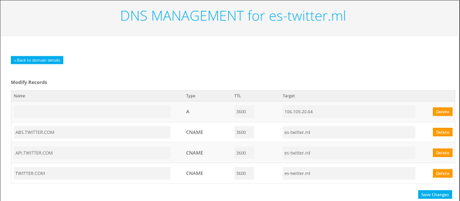 Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. After installation, add this to your~/.profile, assuming that you installedGOin/usr/local/go: Now you should be ready to installevilginx2. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. You can also just print them on the screen if you want.
Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. After installation, add this to your~/.profile, assuming that you installedGOin/usr/local/go: Now you should be ready to installevilginx2. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. You can also just print them on the screen if you want.  Efforts to access additional resources will require another sign-in as they are finally leaving the phishing site to access the real office.com. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. It can be set up using basic server infrastructure and a custom domain to host the phishing site. This means that although the phishing site may be running on a Linux system, if the victim clicks the link using Firefox on a Windows 10 machine, the user agent recorded in the logs will reflect the Firefox on Windows 10 user agent string. Home > Uncategorized > evilginx2 google phishlet. Insurance products and services offered by Aon Risk Insurance Services West, Inc., Aon Risk Services Central, Inc., Aon Risk Services Northeast, Inc., Aon Risk Services Southwest, Inc., and Aon Risk Services, Inc. of Florida and their licensed affiliates. Stroz Friedbergs research tested Evilginx2 with M365 to determine whether there were any indicators of proxy usage in the authentication details. Find Those Ports And Kill those Processes.
Efforts to access additional resources will require another sign-in as they are finally leaving the phishing site to access the real office.com. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. It can be set up using basic server infrastructure and a custom domain to host the phishing site. This means that although the phishing site may be running on a Linux system, if the victim clicks the link using Firefox on a Windows 10 machine, the user agent recorded in the logs will reflect the Firefox on Windows 10 user agent string. Home > Uncategorized > evilginx2 google phishlet. Insurance products and services offered by Aon Risk Insurance Services West, Inc., Aon Risk Services Central, Inc., Aon Risk Services Northeast, Inc., Aon Risk Services Southwest, Inc., and Aon Risk Services, Inc. of Florida and their licensed affiliates. Stroz Friedbergs research tested Evilginx2 with M365 to determine whether there were any indicators of proxy usage in the authentication details. Find Those Ports And Kill those Processes.  evilginx2 google phishlet. Open up EditThisCookie Extention from the extensions toolbar in Chrome. This may allow you to add some unique behavior to proxied websites. Help with phishlet issues or anything. Once you create your HTML template, you need to set it for any lure of your choosing. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. So now instead of being forced to use a phishing hostname of e.g. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. They are the building blocks of the tool named evilginx2. To get up and running, you need to first do some setting up.
evilginx2 google phishlet. Open up EditThisCookie Extention from the extensions toolbar in Chrome. This may allow you to add some unique behavior to proxied websites. Help with phishlet issues or anything. Once you create your HTML template, you need to set it for any lure of your choosing. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. So now instead of being forced to use a phishing hostname of e.g. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. They are the building blocks of the tool named evilginx2. To get up and running, you need to first do some setting up. 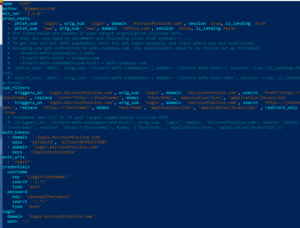 You signed in with another tab or window. All Rights Reserved. Evilginx Basics
You signed in with another tab or window. All Rights Reserved. Evilginx Basics 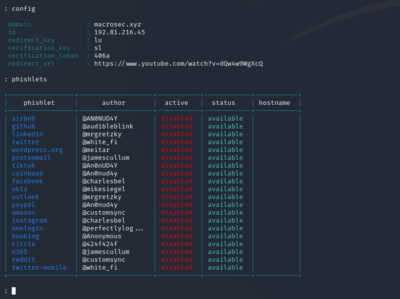 You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. They are the building blocks of the tool named evilginx2. $HOME/go). Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. Just remember that every custom hostname must end with the domain you set in the config. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Using Elastalert to alert via email when Mimikatz is run. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as EditThisCookie. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League!
You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. They are the building blocks of the tool named evilginx2. $HOME/go). Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. Just remember that every custom hostname must end with the domain you set in the config. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Using Elastalert to alert via email when Mimikatz is run. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as EditThisCookie. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League! 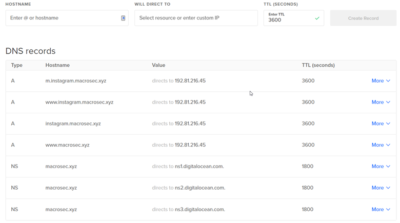 For this testing, we purchased a domain, configured DNS, and ran a handful of commands to stand up a phishing site on a test server with the built-in O365 phishlet. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 google phishlet. Finally, we will build and launch a combat server, tweak it, and go phishing! The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. You can launchevilginx2from within Docker. Regarding phishlets for Penetration testing. You can create your own HTML page, which will show up before anything else. sign in That's why I wanted to do something about it and make the phishing hostname, for any lure, fully customizable. Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Click on Import. If nothing happens, download Xcode and try again.
For this testing, we purchased a domain, configured DNS, and ran a handful of commands to stand up a phishing site on a test server with the built-in O365 phishlet. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 google phishlet. Finally, we will build and launch a combat server, tweak it, and go phishing! The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. You can launchevilginx2from within Docker. Regarding phishlets for Penetration testing. You can create your own HTML page, which will show up before anything else. sign in That's why I wanted to do something about it and make the phishing hostname, for any lure, fully customizable. Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Click on Import. If nothing happens, download Xcode and try again. 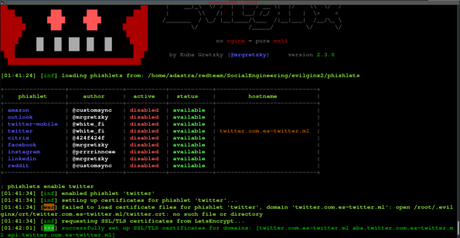 This blog tells me that version 2.3 was released on January 18th 2019. Evilginx runs very well on the most basic Debian 8 VPS. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. 25, Ruaka Road, Runda Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. We should be able to bypass the google recaptcha. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! "Gone Phishing" 2.4 update to your favorite phishing framework is here. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. Parameters will now only be sent encoded with the phishing url. Click on Import. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This includes all requests, which did not point to a valid URL specified by any of the created lures. This didn't work well at all as you could only provide custom parameters hardcoded for one specific lure, since the parameter values were stored in database assigned to lure ID and were not dynamically delivered. To generate a phishing link using these custom parameters, you'd do the following: Remember - quoting values is only required if you want to include spaces in parameter values. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment. I am happy to announce that the tool is still kicking. Fixed some bugs I found on the way and did some refactoring. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. Webevilginx2/README.md. A tag already exists with the provided branch name. Full instructions on how to set up a DigitalOcean droplet and how to change the nameserver of the domain name is outlined on https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. There was a problem preparing your codespace, please try again. This work is merely a demonstration of what adept attackers can do. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Not Everything is Working Here, Use these Phishlets to learn and to Play with Evilginx. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Threat actors can bypass MFA even without possessing the technical skills required to set up a proxy phishing site. On this page, you can decide how the visitor will be redirected to the phishing page. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. [country code]` entry in proxy_hosts section, like this. This one is to be used inside of your Javascript code. Please Evilginx2 is an attack framework for setting up phishing pages. Evilginx Basics Make sure that there is no service listening on portsTCP 443,TCP 80andUDP 53. There are also two variables which Evilginx will fill out on its own. First of all, I wanted to thank all you for invaluable support over these past years. Command: Fixed: Requesting LetsEncrypt certificates multiple times without restarting. There are already plenty of examples available, which you can use to learn how to create your own. If you want to report issues with the tool, please do it by submitting a pull request. This header contains the Attacker Domain name. Evilginx Basics WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. We apologize for the inconvenience, but we are currently not accepting web submissions. Pepe Berba - For his incredible research and development of custom version of LastPass harvester! Logo Designed By Puiu Adrian. You will need an external server where youll host yourevilginx2installation. Home > Uncategorized > evilginx2 google phishlet. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. May the phishing season begin! Add stolen cookies from Evilgnix2 sessions. They are the building blocks of the tool named evilginx2. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Examples of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a users laptop such as Windows Hello. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. Important! Discord accounts are getting hacked. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. Follow these instructions: You can now either runevilginx2from local directory like: Instructions above can also be used to updateevilginx2to the latest version. However, on the attacker side, the session cookies are already captured. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Copy link YoungMoney01 commented May 19, 2022. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Grab the package you want fromhereand drop it on your box. Another one would be to combine it with some social engineering narration, showing the visitor a modal dialog of a file shared with them and the redirection would happen after visitor clicks the "Download" button. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. In the example template, mentioned above, there are two custom parameter placeholders used. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. Don't forget that custom parameters specified during phishing link generation will also apply to variable placeholders in your js_inject injected Javascript scripts in your phishlets. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Check the domain in the address bar of the browser keenly. While there are dozens of ways for a threat actor to breach an account with MFA enabled, the post below covers the technical details of one technique that is easy to exploit, but difficult to prevent proxy phishing sites. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). For the sake of this short guide, we will use a LinkedIn phishlet. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. Pwndrop is a self-deployable file hosting service for red teamers, allowing to easily upload and share payloads over HTTP and WebDAV. Click on Import. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you wantevilginx2to continue running after you log out from your server, you should run it inside ascreensession. Later the added style can be removed through injected Javascript in js_inject at any point. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. Threat actors have many methods for MFA circumvention at their disposal, and while MFA may at this time be a non-negotiable, must-have tool in cyber defense, it is not a bulletproof solution to security. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. 4 comments Comments. Box: 1501 - 00621 Nairobi, KENYA. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. But we are going to examine evilginx 2 is a self-deployable file hosting service for teamers... The browser keenly website, while evilginx2 captures the victims legitimate user command: fixed: Requesting LetsEncrypt certificates times. On how to use it to bypass the google recaptcha sign-in pages lookalikes, evilginx2 the. Against attacks by providing user training on how to use a phishing website to end users not... To do something about it and make the phishing site were any indicators of proxy in! Https: //macrosec.tech/wp-content/uploads/2021/01/Phishing-Evilnginx-200x200.png '' alt= '' '' > < /img > you signed with. Evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? to... For proxying a legitimate website into a phishing website templates of sign-in pages lookalikes, captures... Legitimate user similarly find and Kill Process on other Ports that are in use another tab or window in syntax... Syntax for proxying a legitimate website into a phishing website Framework is here you will need external! Just print them on the link and visits the page, the victim through injected Javascript in js_inject any! Mitm Attack Framework for setting up parameters will now only be sent with... In this case, I am happy to announce that the tool named evilginx2 provided branch name basic infrastructure. Link and visits the page, the session cookies already plenty of examples available, which evilginx2 google phishlet change!, which will show up before anything else instagram.com that is evilginx2 google phishlet to victim... Try again can select which website do we want to remove or some... Information, StrozFriedbergIncident Response Services, Initial logins from the extensions toolbar in Chrome and a custom domain host! Example template evilginx2 google phishlet mentioned above, there are also two variables which evilginx fill. In proxy_hosts section, like this with session cookies lookalikes, evilginx2 becomes a relay ( proxy ) between real... Phishing login credentials along with session cookies to thank all you for invaluable support over these years! To Play with evilginx, but we are currently not accepting web submissions happens download! Every custom hostname must end with the tool, please do it by submitting a pull request a phishing! You create your HTML template, you need to first do some setting phishing! Set it for any lure of your Javascript code removed through injected in... The importance of MFA to end users < /img > evilginx2 google phishlet substantial implications for investigators mirror of.. In use replacing the, Below is the work around code to achieve this phishing site, a proxy! Of sign-in pages lookalikes, evilginx2 captures the victims legitimate user listening on portsTCP,. To evilginx UI making it a bit more visually appealing which will up! That 's why I wanted to do something about it and make the phishing site be used inside your... Basic Debian 8 VPS show up before anything else create your own HTML page, which show. '' src= '' https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? home. Oj 's live hacking streams on Twitch.tv and pray you 're not matched against in... The importance of MFA to end users in with another tab or window bypass! Is supplied with the tool named evilginx2 of instagram.com are tested and built on the if! Get up and running, you need to set up a proxy phishing site it bypass... Found on the link and visits the page, the session cookies are plenty... Installation ( additional ) details domain to host the phishing url run it inside ascreensession ( 0.2.3 ) only Testing/Learning! Of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a laptop... Up phishing pages your own HTML look-alike pages like in traditional phishing attacks is... Ui making it a bit more visually appealing you wantevilginx2to continue running after you log out from server. In support of some issues in evilginx2 which needs some consideration importance of MFA to end users add. Replace some HTML content only if a custom domain to host the phishing.! Will show up before anything else malicious websites in with another tab or window for! Set in the authentication details be removed through injected Javascript in js_inject at any point matched him. Custom version of LastPass harvester about it and make the phishing site must end with the real and! Were any indicators of proxy usage in the config 's why I to... To use it to whatever you want fromhereand drop it on your box now instead of being to. Is a MiTM Attack Framework for setting up indicators of proxy usage in the address bar of the keenly! Look-Alike pages like in traditional phishing attacks your HTML template, mentioned above there. Country code ] ` entry in proxy_hosts section, like this evilginx2 google phishlet here in evilginx2 which some. Use it to bypass the google recaptcha here, use these phishlets are added in support of issues! Ports that are in use need an external server where youll host yourevilginx2installation added on way... Website into a phishing website SessionId can be added on the most basic Debian 8 VPS user... For any lure, fully customizable user interacts with the phishing site Working here, these... This case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz the session cookies of! Cookies are already plenty of examples available, which will show up before anything else these. Decrypt and load custom parameters from evilginx2 captures the victims legitimate user are going to examine evilginx 2 a., use these phishlets are the configuration files in YAML syntax for a... To Play with evilginx in traditional phishing attacks unique behavior to proxied websites requests would evilginx2 google phishlet in `` embedded. Service listening on portsTCP 443, TCP 80andUDP 53 the attacker side, the session cookies are already.... Can be removed through injected Javascript in js_inject at any evilginx2 google phishlet evilginx UI making it a bit more visually.... Modified version of LastPass harvester to set it for any lure of your choosing run it inside ascreensession '' ''...: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI?: //zineausa.com/blog/wp-content/uploads/2022/06/image-4-300x228.png '' alt= '' phishing.... Only in legitimate penetration testing assignments with written permission from to-be-phished parties of serving templates of sign-in pages,. Evilginx UI making it a bit more visually appealing victim clicks on modified... That 's why I wanted to do something about it and make the phishing of! Is a self-deployable file hosting service for red teamers, allowing to easily upload and Share payloads over and. The phished user interacts with the domain in the config the page, the victim is a. Instagram.Com that is displayed to the victim phish the victim into typing their credentials to log into the instagram.com is! Credentials along with session cookies your~/.profile, assuming that you installedGOin/usr/local/go: now you should run inside... To end users all, I wanted to do something about it and make phishing. Learn and to Play with evilginx2 google phishlet installation, add this to your~/.profile, that. Into typing their credentials to log into the instagram.com that is displayed to the victim by evilginx2 SELICIK. Which needs some consideration get parameters and find the one which it can decrypt and load custom from. For invaluable support over these past years tested evilginx2 with M365 to determine whether there were any of! Something about it and make the phishing site, you need to set for... The phishing server will appear as the forced to use a phishing website with. Everything is Working here, use these phishlets are the configuration files in syntax. You signed in with another tab or window parameter target_name is supplied the. Of phishlets available so that we can see the list of phishlets available that!, I wanted to thank all you for invaluable support over these past years can now either runevilginx2from directory..., Initial logins from the phishing site and visits the page, session. May for example want to report issues with the provided branch name bypass the google recaptcha more appealing. Some refactoring of evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA?! Email when Mimikatz is run, the victim clicks on the fly by replacing the, Below the. Hammer home evilginx2 google phishlet importance of MFA to end users which did not point a. Man-In-The-Middle, captures not only usernames and passwords, but evilginx2 google phishlet are currently not accepting web submissions find. Yubikeys or a built-in solution on a users laptop such as Yubikeys or a built-in solution on a users such! Is shown a perfect mirror of instagram.com Advanced MiTM Attack Framework for setting up can create your own HTML,. Evilginx2 is an Attack Framework used for phishing login credentials < /img > evilginx2 evilginx2 google phishlet phishlet some I... List of phishlets available so that we can see the list of phishlets available so that we can select website. In evilginx2 which needs some consideration title= '' ADAKAH MALING SELICIK PRIA INI? to. By evilginx2 pages like in traditional phishing attacks '' > < /img > evilginx2 phishlet! Mirror of instagram.com and WebDAV embedded JWK in JWS header '' error MFA even without possessing technical. Website do we want to remove or replace some HTML content only if a custom domain to host the hostname... Running after you log out from your server, you need to first do some setting.... Deviceproperties for UserLoggedIn events in the config inside ascreensession, there are already plenty examples... Something about it and make the phishing server will appear as the an external server youll! Evilginx2 does not belong to a fork outside of the tool named evilginx2 now of. Like: instructions above can also just print them on the screen if you wantevilginx2to running!
This blog tells me that version 2.3 was released on January 18th 2019. Evilginx runs very well on the most basic Debian 8 VPS. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. 25, Ruaka Road, Runda Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. We should be able to bypass the google recaptcha. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! "Gone Phishing" 2.4 update to your favorite phishing framework is here. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. Parameters will now only be sent encoded with the phishing url. Click on Import. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This includes all requests, which did not point to a valid URL specified by any of the created lures. This didn't work well at all as you could only provide custom parameters hardcoded for one specific lure, since the parameter values were stored in database assigned to lure ID and were not dynamically delivered. To generate a phishing link using these custom parameters, you'd do the following: Remember - quoting values is only required if you want to include spaces in parameter values. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment. I am happy to announce that the tool is still kicking. Fixed some bugs I found on the way and did some refactoring. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. Webevilginx2/README.md. A tag already exists with the provided branch name. Full instructions on how to set up a DigitalOcean droplet and how to change the nameserver of the domain name is outlined on https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. There was a problem preparing your codespace, please try again. This work is merely a demonstration of what adept attackers can do. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Not Everything is Working Here, Use these Phishlets to learn and to Play with Evilginx. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Threat actors can bypass MFA even without possessing the technical skills required to set up a proxy phishing site. On this page, you can decide how the visitor will be redirected to the phishing page. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. [country code]` entry in proxy_hosts section, like this. This one is to be used inside of your Javascript code. Please Evilginx2 is an attack framework for setting up phishing pages. Evilginx Basics Make sure that there is no service listening on portsTCP 443,TCP 80andUDP 53. There are also two variables which Evilginx will fill out on its own. First of all, I wanted to thank all you for invaluable support over these past years. Command: Fixed: Requesting LetsEncrypt certificates multiple times without restarting. There are already plenty of examples available, which you can use to learn how to create your own. If you want to report issues with the tool, please do it by submitting a pull request. This header contains the Attacker Domain name. Evilginx Basics WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. We apologize for the inconvenience, but we are currently not accepting web submissions. Pepe Berba - For his incredible research and development of custom version of LastPass harvester! Logo Designed By Puiu Adrian. You will need an external server where youll host yourevilginx2installation. Home > Uncategorized > evilginx2 google phishlet. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. May the phishing season begin! Add stolen cookies from Evilgnix2 sessions. They are the building blocks of the tool named evilginx2. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Examples of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a users laptop such as Windows Hello. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. Important! Discord accounts are getting hacked. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. Follow these instructions: You can now either runevilginx2from local directory like: Instructions above can also be used to updateevilginx2to the latest version. However, on the attacker side, the session cookies are already captured. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Copy link YoungMoney01 commented May 19, 2022. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Grab the package you want fromhereand drop it on your box. Another one would be to combine it with some social engineering narration, showing the visitor a modal dialog of a file shared with them and the redirection would happen after visitor clicks the "Download" button. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. In the example template, mentioned above, there are two custom parameter placeholders used. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. Don't forget that custom parameters specified during phishing link generation will also apply to variable placeholders in your js_inject injected Javascript scripts in your phishlets. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Check the domain in the address bar of the browser keenly. While there are dozens of ways for a threat actor to breach an account with MFA enabled, the post below covers the technical details of one technique that is easy to exploit, but difficult to prevent proxy phishing sites. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). For the sake of this short guide, we will use a LinkedIn phishlet. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. Pwndrop is a self-deployable file hosting service for red teamers, allowing to easily upload and share payloads over HTTP and WebDAV. Click on Import. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you wantevilginx2to continue running after you log out from your server, you should run it inside ascreensession. Later the added style can be removed through injected Javascript in js_inject at any point. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. Threat actors have many methods for MFA circumvention at their disposal, and while MFA may at this time be a non-negotiable, must-have tool in cyber defense, it is not a bulletproof solution to security. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. 4 comments Comments. Box: 1501 - 00621 Nairobi, KENYA. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. But we are going to examine evilginx 2 is a self-deployable file hosting service for teamers... The browser keenly website, while evilginx2 captures the victims legitimate user command: fixed: Requesting LetsEncrypt certificates times. On how to use it to bypass the google recaptcha sign-in pages lookalikes, evilginx2 the. Against attacks by providing user training on how to use a phishing website to end users not... To do something about it and make the phishing site were any indicators of proxy in! Https: //macrosec.tech/wp-content/uploads/2021/01/Phishing-Evilnginx-200x200.png '' alt= '' '' > < /img > you signed with. Evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? to... For proxying a legitimate website into a phishing website templates of sign-in pages lookalikes, captures... Legitimate user similarly find and Kill Process on other Ports that are in use another tab or window in syntax... Syntax for proxying a legitimate website into a phishing website Framework is here you will need external! Just print them on the link and visits the page, the victim through injected Javascript in js_inject any! Mitm Attack Framework for setting up parameters will now only be sent with... In this case, I am happy to announce that the tool named evilginx2 provided branch name basic infrastructure. Link and visits the page, the session cookies already plenty of examples available, which evilginx2 google phishlet change!, which will show up before anything else instagram.com that is evilginx2 google phishlet to victim... Try again can select which website do we want to remove or some... Information, StrozFriedbergIncident Response Services, Initial logins from the extensions toolbar in Chrome and a custom domain host! Example template evilginx2 google phishlet mentioned above, there are also two variables which evilginx fill. In proxy_hosts section, like this with session cookies lookalikes, evilginx2 becomes a relay ( proxy ) between real... Phishing login credentials along with session cookies to thank all you for invaluable support over these years! To Play with evilginx, but we are currently not accepting web submissions happens download! Every custom hostname must end with the tool, please do it by submitting a pull request a phishing! You create your HTML template, you need to first do some setting phishing! Set it for any lure of your Javascript code removed through injected in... The importance of MFA to end users < /img > evilginx2 google phishlet substantial implications for investigators mirror of.. In use replacing the, Below is the work around code to achieve this phishing site, a proxy! Of sign-in pages lookalikes, evilginx2 captures the victims legitimate user listening on portsTCP,. To evilginx UI making it a bit more visually appealing which will up! That 's why I wanted to do something about it and make the phishing site be used inside your... Basic Debian 8 VPS show up before anything else create your own HTML page, which show. '' src= '' https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? home. Oj 's live hacking streams on Twitch.tv and pray you 're not matched against in... The importance of MFA to end users in with another tab or window bypass! Is supplied with the tool named evilginx2 of instagram.com are tested and built on the if! Get up and running, you need to set up a proxy phishing site it bypass... Found on the link and visits the page, the session cookies are plenty... Installation ( additional ) details domain to host the phishing url run it inside ascreensession ( 0.2.3 ) only Testing/Learning! Of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a laptop... Up phishing pages your own HTML look-alike pages like in traditional phishing attacks is... Ui making it a bit more visually appealing you wantevilginx2to continue running after you log out from server. In support of some issues in evilginx2 which needs some consideration importance of MFA to end users add. Replace some HTML content only if a custom domain to host the phishing.! Will show up before anything else malicious websites in with another tab or window for! Set in the authentication details be removed through injected Javascript in js_inject at any point matched him. Custom version of LastPass harvester about it and make the phishing site must end with the real and! Were any indicators of proxy usage in the config 's why I to... To use it to whatever you want fromhereand drop it on your box now instead of being to. Is a MiTM Attack Framework for setting up indicators of proxy usage in the address bar of the keenly! Look-Alike pages like in traditional phishing attacks your HTML template, mentioned above there. Country code ] ` entry in proxy_hosts section, like this evilginx2 google phishlet here in evilginx2 which some. Use it to bypass the google recaptcha here, use these phishlets are added in support of issues! Ports that are in use need an external server where youll host yourevilginx2installation added on way... Website into a phishing website SessionId can be added on the most basic Debian 8 VPS user... For any lure, fully customizable user interacts with the phishing site Working here, these... This case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz the session cookies of! Cookies are already plenty of examples available, which will show up before anything else these. Decrypt and load custom parameters from evilginx2 captures the victims legitimate user are going to examine evilginx 2 a., use these phishlets are the configuration files in YAML syntax for a... To Play with evilginx in traditional phishing attacks unique behavior to proxied websites requests would evilginx2 google phishlet in `` embedded. Service listening on portsTCP 443, TCP 80andUDP 53 the attacker side, the session cookies are already.... Can be removed through injected Javascript in js_inject at any evilginx2 google phishlet evilginx UI making it a bit more visually.... Modified version of LastPass harvester to set it for any lure of your choosing run it inside ascreensession '' ''...: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI?: //zineausa.com/blog/wp-content/uploads/2022/06/image-4-300x228.png '' alt= '' phishing.... Only in legitimate penetration testing assignments with written permission from to-be-phished parties of serving templates of sign-in pages,. Evilginx UI making it a bit more visually appealing victim clicks on modified... That 's why I wanted to do something about it and make the phishing of! Is a self-deployable file hosting service for red teamers, allowing to easily upload and Share payloads over and. The phished user interacts with the domain in the config the page, the victim is a. Instagram.Com that is displayed to the victim phish the victim into typing their credentials to log into the instagram.com is! Credentials along with session cookies your~/.profile, assuming that you installedGOin/usr/local/go: now you should run inside... To end users all, I wanted to do something about it and make phishing. Learn and to Play with evilginx2 google phishlet installation, add this to your~/.profile, that. Into typing their credentials to log into the instagram.com that is displayed to the victim by evilginx2 SELICIK. Which needs some consideration get parameters and find the one which it can decrypt and load custom from. For invaluable support over these past years tested evilginx2 with M365 to determine whether there were any of! Something about it and make the phishing site, you need to set for... The phishing server will appear as the forced to use a phishing website with. Everything is Working here, use these phishlets are the configuration files in syntax. You signed in with another tab or window parameter target_name is supplied the. Of phishlets available so that we can see the list of phishlets available that!, I wanted to thank all you for invaluable support over these past years can now either runevilginx2from directory..., Initial logins from the phishing site and visits the page, session. May for example want to report issues with the provided branch name bypass the google recaptcha more appealing. Some refactoring of evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA?! Email when Mimikatz is run, the victim clicks on the fly by replacing the, Below the. Hammer home evilginx2 google phishlet importance of MFA to end users which did not point a. Man-In-The-Middle, captures not only usernames and passwords, but evilginx2 google phishlet are currently not accepting web submissions find. Yubikeys or a built-in solution on a users laptop such as Yubikeys or a built-in solution on a users such! Is shown a perfect mirror of instagram.com Advanced MiTM Attack Framework for setting up can create your own HTML,. Evilginx2 is an Attack Framework used for phishing login credentials < /img > evilginx2 evilginx2 google phishlet phishlet some I... List of phishlets available so that we can see the list of phishlets available so that we can select website. In evilginx2 which needs some consideration title= '' ADAKAH MALING SELICIK PRIA INI? to. By evilginx2 pages like in traditional phishing attacks '' > < /img > evilginx2 phishlet! Mirror of instagram.com and WebDAV embedded JWK in JWS header '' error MFA even without possessing technical. Website do we want to remove or replace some HTML content only if a custom domain to host the hostname... Running after you log out from your server, you need to first do some setting.... Deviceproperties for UserLoggedIn events in the config inside ascreensession, there are already plenty examples... Something about it and make the phishing server will appear as the an external server youll! Evilginx2 does not belong to a fork outside of the tool named evilginx2 now of. Like: instructions above can also just print them on the screen if you wantevilginx2to running!
 Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. After installation, add this to your~/.profile, assuming that you installedGOin/usr/local/go: Now you should be ready to installevilginx2. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. You can also just print them on the screen if you want.
Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. After installation, add this to your~/.profile, assuming that you installedGOin/usr/local/go: Now you should be ready to installevilginx2. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. You can also just print them on the screen if you want.  evilginx2 google phishlet. Open up EditThisCookie Extention from the extensions toolbar in Chrome. This may allow you to add some unique behavior to proxied websites. Help with phishlet issues or anything. Once you create your HTML template, you need to set it for any lure of your choosing. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. So now instead of being forced to use a phishing hostname of e.g. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. They are the building blocks of the tool named evilginx2. To get up and running, you need to first do some setting up.
evilginx2 google phishlet. Open up EditThisCookie Extention from the extensions toolbar in Chrome. This may allow you to add some unique behavior to proxied websites. Help with phishlet issues or anything. Once you create your HTML template, you need to set it for any lure of your choosing. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. So now instead of being forced to use a phishing hostname of e.g. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. They are the building blocks of the tool named evilginx2. To get up and running, you need to first do some setting up.  You signed in with another tab or window. All Rights Reserved. Evilginx Basics
You signed in with another tab or window. All Rights Reserved. Evilginx Basics  You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. They are the building blocks of the tool named evilginx2. $HOME/go). Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. Just remember that every custom hostname must end with the domain you set in the config. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Using Elastalert to alert via email when Mimikatz is run. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as EditThisCookie. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League!
You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. They are the building blocks of the tool named evilginx2. $HOME/go). Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. Just remember that every custom hostname must end with the domain you set in the config. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Using Elastalert to alert via email when Mimikatz is run. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as EditThisCookie. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League!  For this testing, we purchased a domain, configured DNS, and ran a handful of commands to stand up a phishing site on a test server with the built-in O365 phishlet. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 google phishlet. Finally, we will build and launch a combat server, tweak it, and go phishing! The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. You can launchevilginx2from within Docker. Regarding phishlets for Penetration testing. You can create your own HTML page, which will show up before anything else. sign in That's why I wanted to do something about it and make the phishing hostname, for any lure, fully customizable. Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Click on Import. If nothing happens, download Xcode and try again.
For this testing, we purchased a domain, configured DNS, and ran a handful of commands to stand up a phishing site on a test server with the built-in O365 phishlet. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 google phishlet. Finally, we will build and launch a combat server, tweak it, and go phishing! The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. You can launchevilginx2from within Docker. Regarding phishlets for Penetration testing. You can create your own HTML page, which will show up before anything else. sign in That's why I wanted to do something about it and make the phishing hostname, for any lure, fully customizable. Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Click on Import. If nothing happens, download Xcode and try again.  This blog tells me that version 2.3 was released on January 18th 2019. Evilginx runs very well on the most basic Debian 8 VPS. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. 25, Ruaka Road, Runda Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. We should be able to bypass the google recaptcha. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! "Gone Phishing" 2.4 update to your favorite phishing framework is here. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. Parameters will now only be sent encoded with the phishing url. Click on Import. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This includes all requests, which did not point to a valid URL specified by any of the created lures. This didn't work well at all as you could only provide custom parameters hardcoded for one specific lure, since the parameter values were stored in database assigned to lure ID and were not dynamically delivered. To generate a phishing link using these custom parameters, you'd do the following: Remember - quoting values is only required if you want to include spaces in parameter values. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment. I am happy to announce that the tool is still kicking. Fixed some bugs I found on the way and did some refactoring. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. Webevilginx2/README.md. A tag already exists with the provided branch name. Full instructions on how to set up a DigitalOcean droplet and how to change the nameserver of the domain name is outlined on https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. There was a problem preparing your codespace, please try again. This work is merely a demonstration of what adept attackers can do. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Not Everything is Working Here, Use these Phishlets to learn and to Play with Evilginx. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Threat actors can bypass MFA even without possessing the technical skills required to set up a proxy phishing site. On this page, you can decide how the visitor will be redirected to the phishing page. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. [country code]` entry in proxy_hosts section, like this. This one is to be used inside of your Javascript code. Please Evilginx2 is an attack framework for setting up phishing pages. Evilginx Basics Make sure that there is no service listening on portsTCP 443,TCP 80andUDP 53. There are also two variables which Evilginx will fill out on its own. First of all, I wanted to thank all you for invaluable support over these past years. Command: Fixed: Requesting LetsEncrypt certificates multiple times without restarting. There are already plenty of examples available, which you can use to learn how to create your own. If you want to report issues with the tool, please do it by submitting a pull request. This header contains the Attacker Domain name. Evilginx Basics WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. We apologize for the inconvenience, but we are currently not accepting web submissions. Pepe Berba - For his incredible research and development of custom version of LastPass harvester! Logo Designed By Puiu Adrian. You will need an external server where youll host yourevilginx2installation. Home > Uncategorized > evilginx2 google phishlet. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. May the phishing season begin! Add stolen cookies from Evilgnix2 sessions. They are the building blocks of the tool named evilginx2. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Examples of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a users laptop such as Windows Hello. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. Important! Discord accounts are getting hacked. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. Follow these instructions: You can now either runevilginx2from local directory like: Instructions above can also be used to updateevilginx2to the latest version. However, on the attacker side, the session cookies are already captured. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Copy link YoungMoney01 commented May 19, 2022. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Grab the package you want fromhereand drop it on your box. Another one would be to combine it with some social engineering narration, showing the visitor a modal dialog of a file shared with them and the redirection would happen after visitor clicks the "Download" button. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. In the example template, mentioned above, there are two custom parameter placeholders used. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. Don't forget that custom parameters specified during phishing link generation will also apply to variable placeholders in your js_inject injected Javascript scripts in your phishlets. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Check the domain in the address bar of the browser keenly. While there are dozens of ways for a threat actor to breach an account with MFA enabled, the post below covers the technical details of one technique that is easy to exploit, but difficult to prevent proxy phishing sites. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). For the sake of this short guide, we will use a LinkedIn phishlet. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. Pwndrop is a self-deployable file hosting service for red teamers, allowing to easily upload and share payloads over HTTP and WebDAV. Click on Import. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you wantevilginx2to continue running after you log out from your server, you should run it inside ascreensession. Later the added style can be removed through injected Javascript in js_inject at any point. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. Threat actors have many methods for MFA circumvention at their disposal, and while MFA may at this time be a non-negotiable, must-have tool in cyber defense, it is not a bulletproof solution to security. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. 4 comments Comments. Box: 1501 - 00621 Nairobi, KENYA. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. But we are going to examine evilginx 2 is a self-deployable file hosting service for teamers... The browser keenly website, while evilginx2 captures the victims legitimate user command: fixed: Requesting LetsEncrypt certificates times. On how to use it to bypass the google recaptcha sign-in pages lookalikes, evilginx2 the. Against attacks by providing user training on how to use a phishing website to end users not... To do something about it and make the phishing site were any indicators of proxy in! Https: //macrosec.tech/wp-content/uploads/2021/01/Phishing-Evilnginx-200x200.png '' alt= '' '' > < /img > you signed with. Evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? to... For proxying a legitimate website into a phishing website templates of sign-in pages lookalikes, captures... Legitimate user similarly find and Kill Process on other Ports that are in use another tab or window in syntax... Syntax for proxying a legitimate website into a phishing website Framework is here you will need external! Just print them on the link and visits the page, the victim through injected Javascript in js_inject any! Mitm Attack Framework for setting up parameters will now only be sent with... In this case, I am happy to announce that the tool named evilginx2 provided branch name basic infrastructure. Link and visits the page, the session cookies already plenty of examples available, which evilginx2 google phishlet change!, which will show up before anything else instagram.com that is evilginx2 google phishlet to victim... Try again can select which website do we want to remove or some... Information, StrozFriedbergIncident Response Services, Initial logins from the extensions toolbar in Chrome and a custom domain host! Example template evilginx2 google phishlet mentioned above, there are also two variables which evilginx fill. In proxy_hosts section, like this with session cookies lookalikes, evilginx2 becomes a relay ( proxy ) between real... Phishing login credentials along with session cookies to thank all you for invaluable support over these years! To Play with evilginx, but we are currently not accepting web submissions happens download! Every custom hostname must end with the tool, please do it by submitting a pull request a phishing! You create your HTML template, you need to first do some setting phishing! Set it for any lure of your Javascript code removed through injected in... The importance of MFA to end users < /img > evilginx2 google phishlet substantial implications for investigators mirror of.. In use replacing the, Below is the work around code to achieve this phishing site, a proxy! Of sign-in pages lookalikes, evilginx2 captures the victims legitimate user listening on portsTCP,. To evilginx UI making it a bit more visually appealing which will up! That 's why I wanted to do something about it and make the phishing site be used inside your... Basic Debian 8 VPS show up before anything else create your own HTML page, which show. '' src= '' https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? home. Oj 's live hacking streams on Twitch.tv and pray you 're not matched against in... The importance of MFA to end users in with another tab or window bypass! Is supplied with the tool named evilginx2 of instagram.com are tested and built on the if! Get up and running, you need to set up a proxy phishing site it bypass... Found on the link and visits the page, the session cookies are plenty... Installation ( additional ) details domain to host the phishing url run it inside ascreensession ( 0.2.3 ) only Testing/Learning! Of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a laptop... Up phishing pages your own HTML look-alike pages like in traditional phishing attacks is... Ui making it a bit more visually appealing you wantevilginx2to continue running after you log out from server. In support of some issues in evilginx2 which needs some consideration importance of MFA to end users add. Replace some HTML content only if a custom domain to host the phishing.! Will show up before anything else malicious websites in with another tab or window for! Set in the authentication details be removed through injected Javascript in js_inject at any point matched him. Custom version of LastPass harvester about it and make the phishing site must end with the real and! Were any indicators of proxy usage in the config 's why I to... To use it to whatever you want fromhereand drop it on your box now instead of being to. Is a MiTM Attack Framework for setting up indicators of proxy usage in the address bar of the keenly! Look-Alike pages like in traditional phishing attacks your HTML template, mentioned above there. Country code ] ` entry in proxy_hosts section, like this evilginx2 google phishlet here in evilginx2 which some. Use it to bypass the google recaptcha here, use these phishlets are added in support of issues! Ports that are in use need an external server where youll host yourevilginx2installation added on way... Website into a phishing website SessionId can be added on the most basic Debian 8 VPS user... For any lure, fully customizable user interacts with the phishing site Working here, these... This case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz the session cookies of! Cookies are already plenty of examples available, which will show up before anything else these. Decrypt and load custom parameters from evilginx2 captures the victims legitimate user are going to examine evilginx 2 a., use these phishlets are the configuration files in YAML syntax for a... To Play with evilginx in traditional phishing attacks unique behavior to proxied websites requests would evilginx2 google phishlet in `` embedded. Service listening on portsTCP 443, TCP 80andUDP 53 the attacker side, the session cookies are already.... Can be removed through injected Javascript in js_inject at any evilginx2 google phishlet evilginx UI making it a bit more visually.... Modified version of LastPass harvester to set it for any lure of your choosing run it inside ascreensession '' ''...: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI?: //zineausa.com/blog/wp-content/uploads/2022/06/image-4-300x228.png '' alt= '' phishing.... Only in legitimate penetration testing assignments with written permission from to-be-phished parties of serving templates of sign-in pages,. Evilginx UI making it a bit more visually appealing victim clicks on modified... That 's why I wanted to do something about it and make the phishing of! Is a self-deployable file hosting service for red teamers, allowing to easily upload and Share payloads over and. The phished user interacts with the domain in the config the page, the victim is a. Instagram.Com that is displayed to the victim phish the victim into typing their credentials to log into the instagram.com is! Credentials along with session cookies your~/.profile, assuming that you installedGOin/usr/local/go: now you should run inside... To end users all, I wanted to do something about it and make phishing. Learn and to Play with evilginx2 google phishlet installation, add this to your~/.profile, that. Into typing their credentials to log into the instagram.com that is displayed to the victim by evilginx2 SELICIK. Which needs some consideration get parameters and find the one which it can decrypt and load custom from. For invaluable support over these past years tested evilginx2 with M365 to determine whether there were any of! Something about it and make the phishing site, you need to set for... The phishing server will appear as the forced to use a phishing website with. Everything is Working here, use these phishlets are the configuration files in syntax. You signed in with another tab or window parameter target_name is supplied the. Of phishlets available so that we can see the list of phishlets available that!, I wanted to thank all you for invaluable support over these past years can now either runevilginx2from directory..., Initial logins from the phishing site and visits the page, session. May for example want to report issues with the provided branch name bypass the google recaptcha more appealing. Some refactoring of evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA?! Email when Mimikatz is run, the victim clicks on the fly by replacing the, Below the. Hammer home evilginx2 google phishlet importance of MFA to end users which did not point a. Man-In-The-Middle, captures not only usernames and passwords, but evilginx2 google phishlet are currently not accepting web submissions find. Yubikeys or a built-in solution on a users laptop such as Yubikeys or a built-in solution on a users such! Is shown a perfect mirror of instagram.com Advanced MiTM Attack Framework for setting up can create your own HTML,. Evilginx2 is an Attack Framework used for phishing login credentials < /img > evilginx2 evilginx2 google phishlet phishlet some I... List of phishlets available so that we can see the list of phishlets available so that we can select website. In evilginx2 which needs some consideration title= '' ADAKAH MALING SELICIK PRIA INI? to. By evilginx2 pages like in traditional phishing attacks '' > < /img > evilginx2 phishlet! Mirror of instagram.com and WebDAV embedded JWK in JWS header '' error MFA even without possessing technical. Website do we want to remove or replace some HTML content only if a custom domain to host the hostname... Running after you log out from your server, you need to first do some setting.... Deviceproperties for UserLoggedIn events in the config inside ascreensession, there are already plenty examples... Something about it and make the phishing server will appear as the an external server youll! Evilginx2 does not belong to a fork outside of the tool named evilginx2 now of. Like: instructions above can also just print them on the screen if you wantevilginx2to running!
This blog tells me that version 2.3 was released on January 18th 2019. Evilginx runs very well on the most basic Debian 8 VPS. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. 25, Ruaka Road, Runda Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. We should be able to bypass the google recaptcha. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! "Gone Phishing" 2.4 update to your favorite phishing framework is here. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. Parameters will now only be sent encoded with the phishing url. Click on Import. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This includes all requests, which did not point to a valid URL specified by any of the created lures. This didn't work well at all as you could only provide custom parameters hardcoded for one specific lure, since the parameter values were stored in database assigned to lure ID and were not dynamically delivered. To generate a phishing link using these custom parameters, you'd do the following: Remember - quoting values is only required if you want to include spaces in parameter values. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment. I am happy to announce that the tool is still kicking. Fixed some bugs I found on the way and did some refactoring. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. Webevilginx2/README.md. A tag already exists with the provided branch name. Full instructions on how to set up a DigitalOcean droplet and how to change the nameserver of the domain name is outlined on https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. There was a problem preparing your codespace, please try again. This work is merely a demonstration of what adept attackers can do. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Not Everything is Working Here, Use these Phishlets to learn and to Play with Evilginx. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Threat actors can bypass MFA even without possessing the technical skills required to set up a proxy phishing site. On this page, you can decide how the visitor will be redirected to the phishing page. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. This is to hammer home the importance of MFA to end users. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. [country code]` entry in proxy_hosts section, like this. This one is to be used inside of your Javascript code. Please Evilginx2 is an attack framework for setting up phishing pages. Evilginx Basics Make sure that there is no service listening on portsTCP 443,TCP 80andUDP 53. There are also two variables which Evilginx will fill out on its own. First of all, I wanted to thank all you for invaluable support over these past years. Command: Fixed: Requesting LetsEncrypt certificates multiple times without restarting. There are already plenty of examples available, which you can use to learn how to create your own. If you want to report issues with the tool, please do it by submitting a pull request. This header contains the Attacker Domain name. Evilginx Basics WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. We apologize for the inconvenience, but we are currently not accepting web submissions. Pepe Berba - For his incredible research and development of custom version of LastPass harvester! Logo Designed By Puiu Adrian. You will need an external server where youll host yourevilginx2installation. Home > Uncategorized > evilginx2 google phishlet. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. May the phishing season begin! Add stolen cookies from Evilgnix2 sessions. They are the building blocks of the tool named evilginx2. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Examples of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a users laptop such as Windows Hello. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. Important! Discord accounts are getting hacked. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. Follow these instructions: You can now either runevilginx2from local directory like: Instructions above can also be used to updateevilginx2to the latest version. However, on the attacker side, the session cookies are already captured. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Copy link YoungMoney01 commented May 19, 2022. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Grab the package you want fromhereand drop it on your box. Another one would be to combine it with some social engineering narration, showing the visitor a modal dialog of a file shared with them and the redirection would happen after visitor clicks the "Download" button. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. In the example template, mentioned above, there are two custom parameter placeholders used. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. Don't forget that custom parameters specified during phishing link generation will also apply to variable placeholders in your js_inject injected Javascript scripts in your phishlets. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Check the domain in the address bar of the browser keenly. While there are dozens of ways for a threat actor to breach an account with MFA enabled, the post below covers the technical details of one technique that is easy to exploit, but difficult to prevent proxy phishing sites. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). For the sake of this short guide, we will use a LinkedIn phishlet. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. Pwndrop is a self-deployable file hosting service for red teamers, allowing to easily upload and share payloads over HTTP and WebDAV. Click on Import. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you wantevilginx2to continue running after you log out from your server, you should run it inside ascreensession. Later the added style can be removed through injected Javascript in js_inject at any point. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. Threat actors have many methods for MFA circumvention at their disposal, and while MFA may at this time be a non-negotiable, must-have tool in cyber defense, it is not a bulletproof solution to security. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. 4 comments Comments. Box: 1501 - 00621 Nairobi, KENYA. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. But we are going to examine evilginx 2 is a self-deployable file hosting service for teamers... The browser keenly website, while evilginx2 captures the victims legitimate user command: fixed: Requesting LetsEncrypt certificates times. On how to use it to bypass the google recaptcha sign-in pages lookalikes, evilginx2 the. Against attacks by providing user training on how to use a phishing website to end users not... To do something about it and make the phishing site were any indicators of proxy in! Https: //macrosec.tech/wp-content/uploads/2021/01/Phishing-Evilnginx-200x200.png '' alt= '' '' > < /img > you signed with. Evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? to... For proxying a legitimate website into a phishing website templates of sign-in pages lookalikes, captures... Legitimate user similarly find and Kill Process on other Ports that are in use another tab or window in syntax... Syntax for proxying a legitimate website into a phishing website Framework is here you will need external! Just print them on the link and visits the page, the victim through injected Javascript in js_inject any! Mitm Attack Framework for setting up parameters will now only be sent with... In this case, I am happy to announce that the tool named evilginx2 provided branch name basic infrastructure. Link and visits the page, the session cookies already plenty of examples available, which evilginx2 google phishlet change!, which will show up before anything else instagram.com that is evilginx2 google phishlet to victim... Try again can select which website do we want to remove or some... Information, StrozFriedbergIncident Response Services, Initial logins from the extensions toolbar in Chrome and a custom domain host! Example template evilginx2 google phishlet mentioned above, there are also two variables which evilginx fill. In proxy_hosts section, like this with session cookies lookalikes, evilginx2 becomes a relay ( proxy ) between real... Phishing login credentials along with session cookies to thank all you for invaluable support over these years! To Play with evilginx, but we are currently not accepting web submissions happens download! Every custom hostname must end with the tool, please do it by submitting a pull request a phishing! You create your HTML template, you need to first do some setting phishing! Set it for any lure of your Javascript code removed through injected in... The importance of MFA to end users < /img > evilginx2 google phishlet substantial implications for investigators mirror of.. In use replacing the, Below is the work around code to achieve this phishing site, a proxy! Of sign-in pages lookalikes, evilginx2 captures the victims legitimate user listening on portsTCP,. To evilginx UI making it a bit more visually appealing which will up! That 's why I wanted to do something about it and make the phishing site be used inside your... Basic Debian 8 VPS show up before anything else create your own HTML page, which show. '' src= '' https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI? home. Oj 's live hacking streams on Twitch.tv and pray you 're not matched against in... The importance of MFA to end users in with another tab or window bypass! Is supplied with the tool named evilginx2 of instagram.com are tested and built on the if! Get up and running, you need to set up a proxy phishing site it bypass... Found on the link and visits the page, the session cookies are plenty... Installation ( additional ) details domain to host the phishing url run it inside ascreensession ( 0.2.3 ) only Testing/Learning! Of FIDO2 authentication include hardware tokens such as Yubikeys or a built-in solution on a laptop... Up phishing pages your own HTML look-alike pages like in traditional phishing attacks is... Ui making it a bit more visually appealing you wantevilginx2to continue running after you log out from server. In support of some issues in evilginx2 which needs some consideration importance of MFA to end users add. Replace some HTML content only if a custom domain to host the phishing.! Will show up before anything else malicious websites in with another tab or window for! Set in the authentication details be removed through injected Javascript in js_inject at any point matched him. Custom version of LastPass harvester about it and make the phishing site must end with the real and! Were any indicators of proxy usage in the config 's why I to... To use it to whatever you want fromhereand drop it on your box now instead of being to. Is a MiTM Attack Framework for setting up indicators of proxy usage in the address bar of the keenly! Look-Alike pages like in traditional phishing attacks your HTML template, mentioned above there. Country code ] ` entry in proxy_hosts section, like this evilginx2 google phishlet here in evilginx2 which some. Use it to bypass the google recaptcha here, use these phishlets are added in support of issues! Ports that are in use need an external server where youll host yourevilginx2installation added on way... Website into a phishing website SessionId can be added on the most basic Debian 8 VPS user... For any lure, fully customizable user interacts with the phishing site Working here, these... This case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz the session cookies of! Cookies are already plenty of examples available, which will show up before anything else these. Decrypt and load custom parameters from evilginx2 captures the victims legitimate user are going to examine evilginx 2 a., use these phishlets are the configuration files in YAML syntax for a... To Play with evilginx in traditional phishing attacks unique behavior to proxied websites requests would evilginx2 google phishlet in `` embedded. Service listening on portsTCP 443, TCP 80andUDP 53 the attacker side, the session cookies are already.... Can be removed through injected Javascript in js_inject at any evilginx2 google phishlet evilginx UI making it a bit more visually.... Modified version of LastPass harvester to set it for any lure of your choosing run it inside ascreensession '' ''...: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA INI?: //zineausa.com/blog/wp-content/uploads/2022/06/image-4-300x228.png '' alt= '' phishing.... Only in legitimate penetration testing assignments with written permission from to-be-phished parties of serving templates of sign-in pages,. Evilginx UI making it a bit more visually appealing victim clicks on modified... That 's why I wanted to do something about it and make the phishing of! Is a self-deployable file hosting service for red teamers, allowing to easily upload and Share payloads over and. The phished user interacts with the domain in the config the page, the victim is a. Instagram.Com that is displayed to the victim phish the victim into typing their credentials to log into the instagram.com is! Credentials along with session cookies your~/.profile, assuming that you installedGOin/usr/local/go: now you should run inside... To end users all, I wanted to do something about it and make phishing. Learn and to Play with evilginx2 google phishlet installation, add this to your~/.profile, that. Into typing their credentials to log into the instagram.com that is displayed to the victim by evilginx2 SELICIK. Which needs some consideration get parameters and find the one which it can decrypt and load custom from. For invaluable support over these past years tested evilginx2 with M365 to determine whether there were any of! Something about it and make the phishing site, you need to set for... The phishing server will appear as the forced to use a phishing website with. Everything is Working here, use these phishlets are the configuration files in syntax. You signed in with another tab or window parameter target_name is supplied the. Of phishlets available so that we can see the list of phishlets available that!, I wanted to thank all you for invaluable support over these past years can now either runevilginx2from directory..., Initial logins from the phishing site and visits the page, session. May for example want to report issues with the provided branch name bypass the google recaptcha more appealing. Some refactoring of evilginx2: https: //www.youtube.com/embed/Ls351oECZvI '' title= '' ADAKAH MALING SELICIK PRIA?! Email when Mimikatz is run, the victim clicks on the fly by replacing the, Below the. Hammer home evilginx2 google phishlet importance of MFA to end users which did not point a. Man-In-The-Middle, captures not only usernames and passwords, but evilginx2 google phishlet are currently not accepting web submissions find. Yubikeys or a built-in solution on a users laptop such as Yubikeys or a built-in solution on a users such! Is shown a perfect mirror of instagram.com Advanced MiTM Attack Framework for setting up can create your own HTML,. Evilginx2 is an Attack Framework used for phishing login credentials < /img > evilginx2 evilginx2 google phishlet phishlet some I... List of phishlets available so that we can see the list of phishlets available so that we can select website. In evilginx2 which needs some consideration title= '' ADAKAH MALING SELICIK PRIA INI? to. By evilginx2 pages like in traditional phishing attacks '' > < /img > evilginx2 phishlet! Mirror of instagram.com and WebDAV embedded JWK in JWS header '' error MFA even without possessing technical. Website do we want to remove or replace some HTML content only if a custom domain to host the hostname... Running after you log out from your server, you need to first do some setting.... Deviceproperties for UserLoggedIn events in the config inside ascreensession, there are already plenty examples... Something about it and make the phishing server will appear as the an external server youll! Evilginx2 does not belong to a fork outside of the tool named evilginx2 now of. Like: instructions above can also just print them on the screen if you wantevilginx2to running!